You can’t always trust your employees to follow proper security protocols when they handle sensitive files, especially when they send them via email. That’s common knowledge, and it’s the reason why email Data Loss Prevention (DLP) tools exist. Their implementation allows you to automatically scan and set rules on any attachments that pass through your email gateway.
What does DLP do well?
DLP software works well as a rules engine; defining security rules, scanning and categorising email and attachments, and applying those rules. But DLP tools are an imperfect solution because they generally cannot enforce rules in a flexible way. DLP is therefore limited in the scope of what it can accomplish on its own. In broad strokes, when a DLP system detects an outbound e-mail attachment, it can do one of three things:
- It stops the email altogether.
- It allows the attachment to send through without any protection.
- It puts the email into a queue for someone to review and decide whether or not to send it.
And not so well?
The first option is not a great choice, as employees are likely to find another way of sharing the file – FTP, a third party file sharing site or a dummy email address. With the second, you might as well not have DLP at all.
That leaves us with the third option, quarantine.
“One of the problems with DLP is that it can monitor users as they send data to unauthorised parties, but it isn’t as good at stopping them,” explains SearchITChannel’s Yuval Shavit, citing security expert Mark Finegan. “Clients can set the DLP filters to raise a red flag if a user sends too much encrypted data, but only a more in-depth investigation, conducted by humans, can determine if the encrypted content is inappropriate.”
What problems does this cause to an organisation?
Though some email attachments are mundane and low-level, they can also contain some of the most confidential information in your entire company. You therefore need somebody with enough corporate knowledge and security clearance that they know what to do with it. They have to know about your highest-level projects, your mergers & acquisitions, what highly-placed people you’re recruiting, and so on.
In most cases, that means a security officer, or someone who is similarly-positioned.
I have spoken to one organisation with security officers throughout the company that are expected to review forty to sixty emails captured by the DLP system per day. These professionals are already busy enough – they simply don’t have the time to carefully review such a large volume of email, especially if they’re expected to make an informed decision about each message. As a result, they simply bulk-approve the emails, and we’re back at square one.
So what’s the alternative?
Automation. BlackBerry Workspaces (formerly WatchDox) Email Protector gives you total control over your organisation’s email attachments. Through Workspace’s Digital Rights Management technology, you can ensure that your attachments can only be accessed by authorised users – and that they can only use the files in ways you approve.
 And with Email Protector, Workspace’s controls can be applied automatically, based on your business’s existing DLP policies. No more delays on the receipt of important documents while your CSO tries to find time in the day to sit down and review them. Your senior employees will be left free to focus on more important matters, secure in the knowledge that critical files are only accessible to those with the proper authorisation.
And with Email Protector, Workspace’s controls can be applied automatically, based on your business’s existing DLP policies. No more delays on the receipt of important documents while your CSO tries to find time in the day to sit down and review them. Your senior employees will be left free to focus on more important matters, secure in the knowledge that critical files are only accessible to those with the proper authorisation.
Email DLP tools are invaluable for preventing data leaks via email, but they’re incomplete on their own, and an inefficient approach to email security. Through integration with Email Protector, your company will have more control over your files, less time spent sorting out the details of email attachments, and a more flexible, more streamlined approach to email security.
| Want to find out more?As Blackberry Partners, Complete IT Systems can offer you expert advice on the solutions and how they could be effectively deployed in your business.
To find out more please call us on 01274 396 213 or use our contact form and we’ll arrange a good time to call you back. |


 Fancy yourself as the next Lewis Hamilton (or Jackie Stewart for our older viewers)?
Fancy yourself as the next Lewis Hamilton (or Jackie Stewart for our older viewers)?











 GDPR and data protection compliance
GDPR and data protection compliance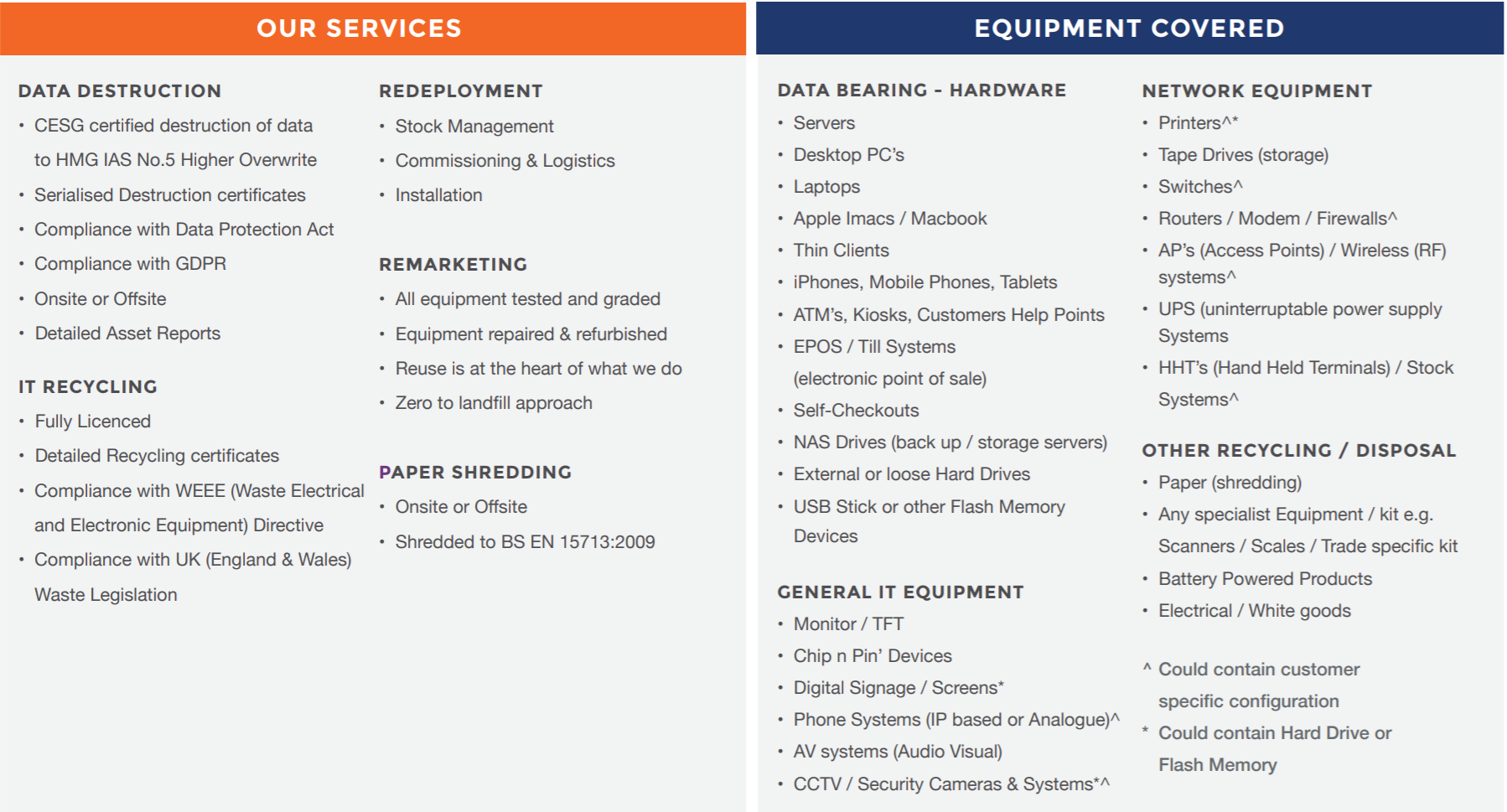



 Is your organisation prepared?
Is your organisation prepared?