There is often confusion between the two complementary processes of data backup and information archiving. In this article, we compare them and discuss the specific needs addressed by each one.
We also review why organisations continue to need both a backup and an archiving solution even after they have moved to Microsoft Office 365.
Comparing Backup and Archiving
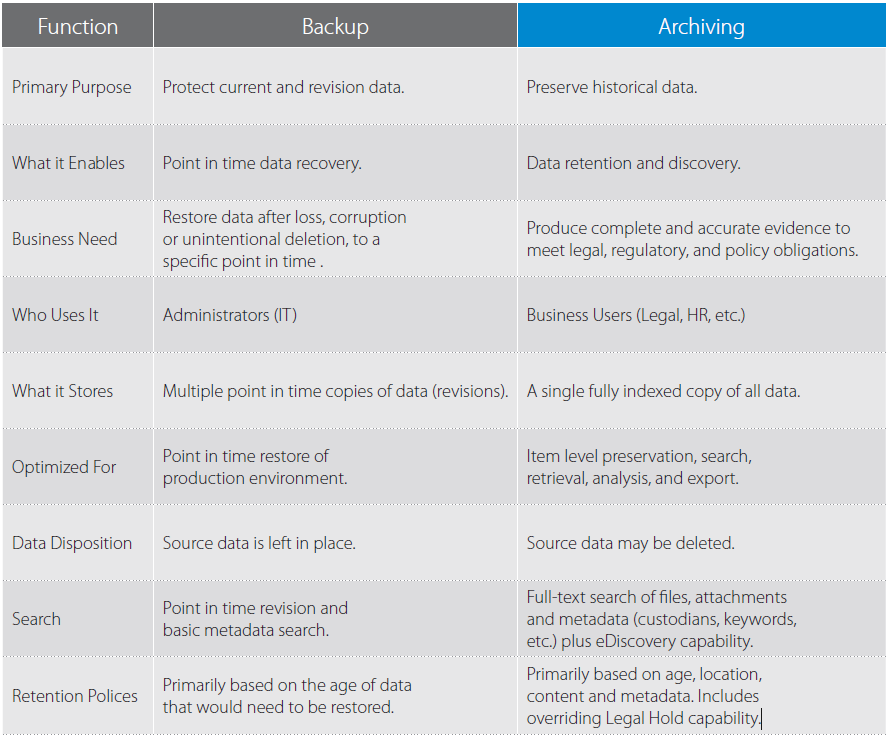
Backups and archives both store copies of data from the production environment, but the use cases for each are different, which means that different solutions are appropriate for each. A backup enables recovery from a situation where data has been lost, corrupted or becomes inaccessible, so it’s primarily a safeguard to facilitate data recovery. A backup stores multiple copies that are each associated with a specific revision of data, and it provides recovery back to a known good state from a specific point of time.
An archive enables compliance with legal and business data retention policies, as well as supporting eDiscovery. An archive preserves a single copy in secure immutable storage for a finite time period and provides ongoing end user access to historical business information.
This table summarises some of the key differences between backup and archiving:
For effective data protection and preservation, organisations need both a backup and an archiving strategy. They may attempt to use a backup solution as an archive (and vice versa), but as will be discussed below, there are significant limitations and deficiencies with this approach that make it inadvisable.
Backup is for Recovery
The primary purpose of backup is to allow recovery from the situation where the original version of data is lost due to unintentional or accidental deletion, or where files have been corrupted in some way to make it unusable.
A backup system achieves this by taking copies of the data on a regular basis to create a series of revisions. Each one of these revisions reflects the data at a specified point in time and can be restored back as needed.
Most backup copies are retained only for a few days or weeks with later copies superseding previous versions. However, it is common for one version to be retained semi-permanently on a weekly or monthly basis to allow data to be recovered from a much earlier point in time. For email data in particular, backup solutions are typically used to protect the most recent data, as this tends to be the most relevant for end users.
I have Office 365, why do I need to back it up?
Accidental deletion by users is the most frequent cause of data loss in a SaaS environment such as Microsoft Office 365; however, there are other ways where data can be lost. Application errors or mistakes in processing can cause data to be lost or overwritten, and there is always the risk of malicious deletion by employees with access to the data. A threat that has come to prominence recently is ransomware, which encrypts data and renders it inaccessible. Office 365 itself focuses primarily on ensuring that service and data availability is not disrupted, but Microsoft does provide customers two options for data recovery:
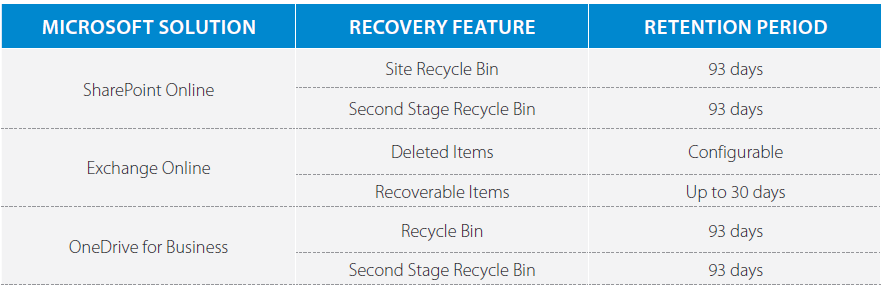
- Recycle Bin: Data that has been recently deleted by users can be recovered from the Recycle Bin (for OneDrive), or the Deleted Items and Recoverable Items folders (for Exchange Online). However, these are subject to retention periods as listed below, after which data is permanently deleted and no longer available.
- Document Versioning: If the Document Versioning feature is turned on, OneDrive for Business will retain a number of previous versions of each document that has been amended, and end users are then able to restore back to any of these previous versions. However, this does not provide protection against unintentional or accidental deletion, as all versions of a document are removed when the current version is deleted.
Organisations adopting Office 365 should recognise that there are serious limitations inherent in both of these options:
- These options operate at an individual item level, so they are not suitable for the recovery of
larger quantities of data such as entire folders or mailboxes.
- It is not feasible to do a point in time data restore using either of these options without
considerable additional processing.
In our next article, we’ll look in more detail at the problems of using backup as an archive.
How can I find out more?
As Barracuda Partners, Complete IT Systems can offer you expert advice on the solutions and how they could be effectively deployed in your business.
To find out more please call us on 01274 396 213 or use our contact form and we’ll arrange a good time to call you back.