Arguably, the cyber security industry has never had a more important role to play than keeping mission-critical organisations and agencies safe from cyber attacks during the COVID-19 pandemic.
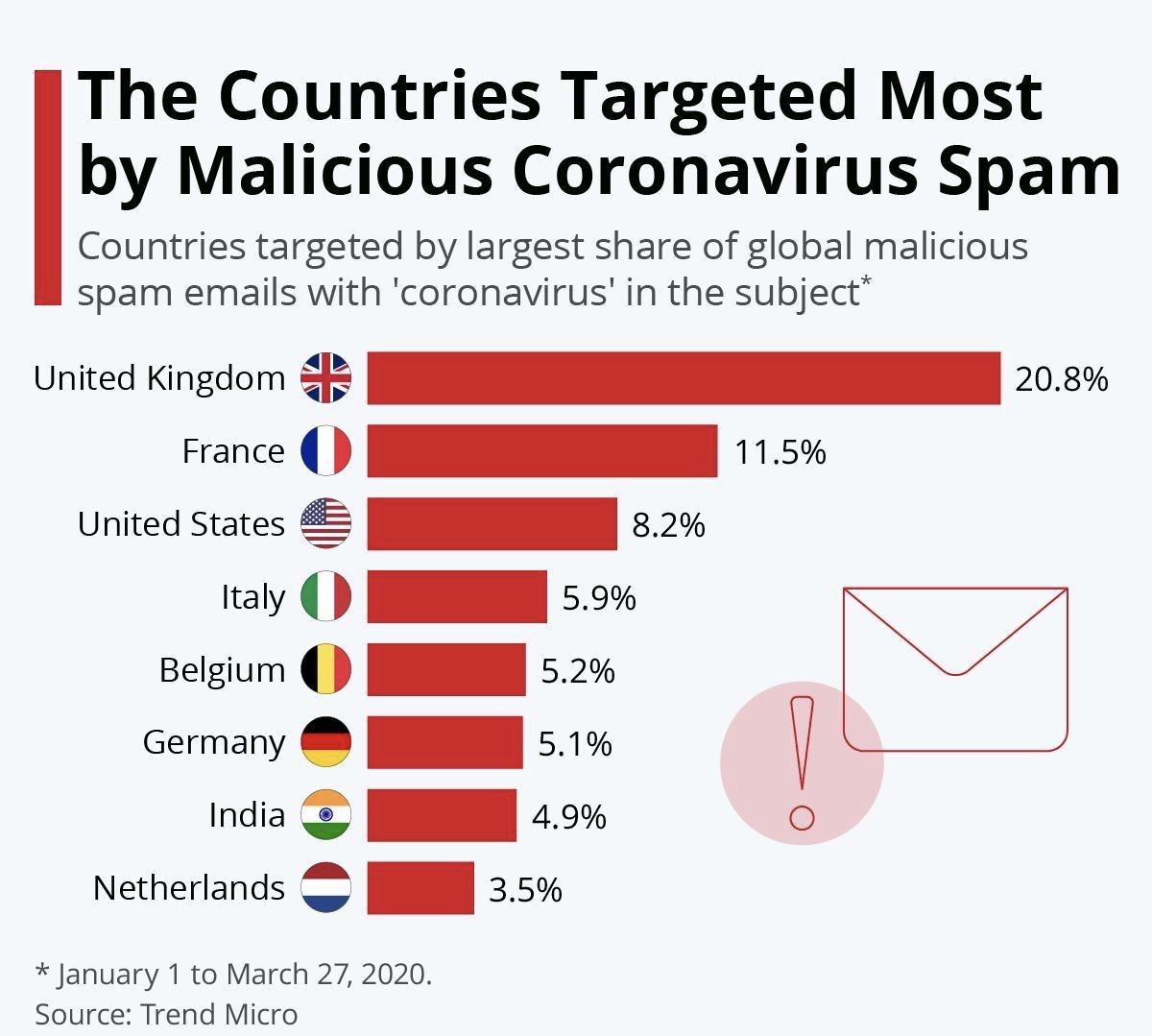
And this is especially true for the UK, which has by far the highest number of reported instances in the world of malicious spam emails with ‘coronavirus’ in the subject line.
This article was previously published here. On our COVID-19 resource hub, we have a range of cyber security options and services to keep your business’ valuable data safe on cloud applications, including BitDam for Microsoft Teams and Zoom, Barracuda firewalls, and Datto SaaS Protection for Office 365.
Cyber threat actors are actively attacking the World Health Organisation (WHO) and there has been a rise in scams touting fake cures for the novel coronavirus, said Paul Dwyer, CEO of Dublin-based Cyber Risk International, which specialises in developing corporate cyber defence programs. Dwyer was the guest on this week’s edition of Task Force Seven Radio, with host, George Rettas, the president and CEO of Task Force Seven Radio and Task Force Seven Technologies.
At the same time as the attacks are occurring, “we’re also seeing the ingenuity, the collaboration, the people putting egos to one side and just trying to work together to come up with solutions,’’ said Dwyer, who is also president of the International Cyber Threat Task Force.
He said cyber security professionals play an integral role in helping find a cure for the coronavirus. “At the end of the day, the solution is going to come from a line of code or some sort of system that has been supported from an IT perspective, and that means that it has to be secure,’’ Dwyer said.
There is also a realisation “that national borders don’t matter anymore,’’ he said. “It’s about humanity being connected and trying to deal with this threat, and the solution will lie in the ability to be able to communicate effectively, to be able to analyse data, to be able to distinguish between fake and real and be able to end this. I do believe it’s bringing out the best and the worst in people.”
Noting that there is a huge focus on hand washing right now, Rettas asked Dwyer to discuss the parallels that can be drawn between that and good cyber hygiene.
Just as there are contagion factors that can be caused by someone who is infected with the coronavirus, Dwyer said, a system can be infected malware when basic controls such as patching and applying updates are not practiced.
One small player can cause a widespread cyberattack, Dwyer said.
“I’m unfortunately putting out a bit of a negative message, a warning, to people saying all these bad guys … have been holding off,’’ he said. Then he issued a dire prediction.
“The big one is going to happen in relation to the financial sector in particular, because [hackers are] highly organised … The general defences of cyber hygiene stops most attacks as we all know, but the big organised guys, — we can see that they’re rubbing their hands and they’re getting ready to make moves and more sophisticated moves on the larger targets.”
But beyond the financial sector, Dwyer said he believes healthcare remains a big target too.
The Geopolitics Of Cyber Security
The conversation then turned political and after Dwyer mentioned he has interviewed National Security Agency whistleblower Edward Snowden, Rettas said he couldn’t “ squander the opportunity” and asked Dwyer for his thoughts about Snowden’s actions.
“I think he did the world a favour,’’ Dwyer replied. “I’ve interviewed him twice. Supremely nice and intelligent guy … I understand his motivations and his passion.”
Dwyer went on to say that Snowden brought “attention to the fact that things were going on that shouldn’t be going on,” and that “he’s done the world a favour and he’s given us a chance to reflect upon privacy,” which he said he advocates for.
In response to a question by Rettas about Snowden’s future, Dwyer said he believes he’s willing to come back to the US “as long as there’s a guarantee that he won’t be tortured.” He added that depending on becomes president after the 2020 election, he might even be pardoned.
Rettas then pivoted the conversation back to the fact that geopolitics plays a big role not only in issues like that, but in the country’s response to the COVID-19 virus as well. He asked whether it’s important for a CISO to understand geopolitics?
Dwyer responded that it absolutely is and noted that a lot of hackers’ actions are motivated by “national pride.”
He likened hackers to “being on the Olympic team of their country,” and said that “when we saw lots of hacking coming in from China and … still do obviously, a lot of this was about nationalistic pride. It wasn’t about making money. It wasn’t about scam artists … whether it was Russia, whether it was Nigeria, a lot of it was just about nationalistic pride.”
Dwyer also said he thinks in every crisis and every challenge, there’s an opportunity, and the COVID-19 virus presents both.
When he founded the International Cyber Threat Task Force, he said that “one of the goals was to form an organisation where all the good guys can work together” and share knowledge with “the right kinds of people” and train together with the goal of disrupting cyber attackers.
CISOs And Risk Management
Rettas noted that Dwyer advises CISOs all over the world, and that risk is a big part of their jobs, “but effective CISOs really map the residual risk of controls back to their business objectives.” This is a language that corporate boards understand, Rettas pointed out, and it also helps the CISO gain credibility. He asked Dwyer to discuss how a CISO determines what metrics should be communicated to the board and how the net message should be crafted? And, if a CISO is not a risk professional, can they even do their job?
Dwyer said that meaningful metrics are when a CISO is able to tie any residual risk identified back to the key objectives of the business. “So, if the business objective is it wants to roll out a new app or it wants to get X thousand customers onto an online system, and you’ve identified that there are cyber risks around that and you’re able to quantify those — not subjectively, but empirically actually put numbers on those and have science behind it — then the business will eat that up.”
The solution, he continued, “is to marry the principles of security risk management.” That means have security practices around confidentiality, integrity, and availability, and incorporating them into a risk management program that the business will understand, he said. To make this happen, CISOs absolutely have to understand the business they are in, Dwyer stressed. It’s not enough to say, “Oh, I’m business aligned. They don’t even know what business aligned means,” he said.
Admitting that what he was about to say makes him “lose friends,” Dwyer then posited that “cybersecurity doesn’t belong to the CISO. It belongs to the CEO … I always feel that cybersecurity should be integrated as part of the enterprise risk management program.”
And, he added that a CISO should not be working under the CIO since they’re trying to innovate and keep systems running.
A CISO should report to the enterprise risk manager, and ultimately, the executive board and the CEO, Dwyer said.
At the end of the day, the CISO “is as much a salesperson as a politician, as a subject matter expert. And it’s a business leader position,’’ he said. “That person needs to be able to sell ideas within the organisation … be able to collaborate, be able to join people together with different opinions, to be able to support and understand the business model.”
A CISO is “sometimes a person with a big personality, sometimes a person that’s good with people, a good communicator, good business [savvy],’’ he added. “They’re very important skills that a CISO should have.”
Help during the COVID-19 crisis
The expert team at Complete IT Systems are publishing a series of guidance and tips to help you and your business through this situation. This covers all aspects of quickly providing safe, comfortable and efficient home offices for your users, including data security, collaboration tools, laptops, desktops, print and consumables, support for critical IT tasks, and more. Click here for our central COVID-19 resource hub.





