Cloud-to-cloud backup – why you should backup Microsoft 365 data
What is the use case for cloud-to-cloud backup? Despite the misconception to the contrary, Microsoft 365 is not a backup tool. Instead, it should be thought of as providing availability for users to conveniently access documents – but not a secure backup archive.
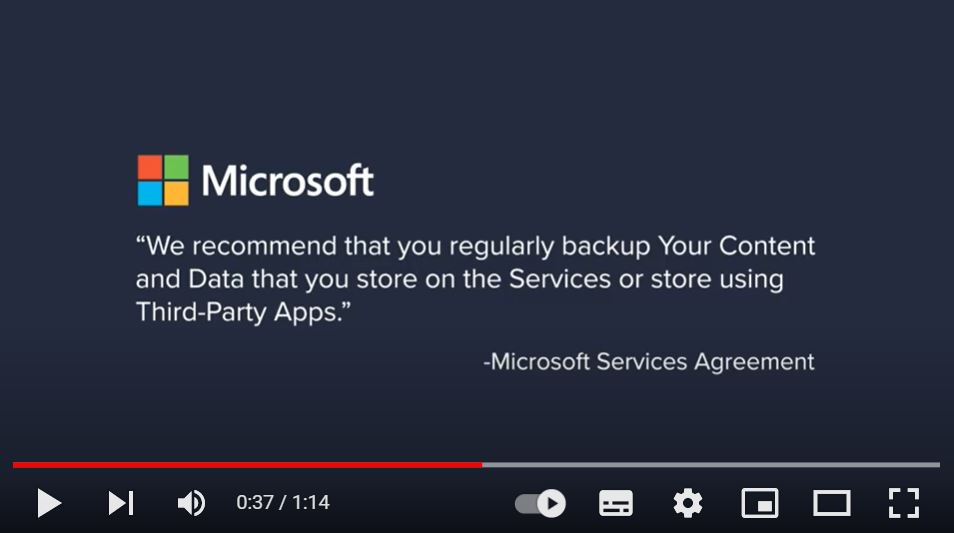
Microsoft’s own user agreement confirms that it actually provides extremely limited data protection by retaining deleted items in site collection bins. These are very similar to the recycle bin on Windows Desktops. However, files are only retained for a maximum of 93 days. The retention of files in Microsoft Teams can be even more limited, with Teams channels only protected for 21 days.
The implications for IT
Restoring entire users’ folders or mailboxes can be a tedious, manual process. If the data is mission-critical, this will inevitably mean that widespread disruption can be caused.
Because of this, Microsoft itself recommends that you its customers use third-party backup for data hosted in Office 365.
What is the solution?
Cloud-to-Cloud Backup provides comprehensive, cost-effective, scalable protection for your organisation’s 365 data.
Barracuda Cloud-to-Cloud Backup offers fast backups, highly granular restore capabilities, and unmatched ease of use. It automatically backs up all data from email, OneDrive for Business, SharePoint Online, Groups, and Teams data to the Barracuda Cloud.
The service is provided as a complete Software as a Service (SaaS) offering so no hardware or software to deploy or manage, and when time is of the essence, restoring what you need takes just a few clicks.
Find out how to go from signing up to running your first backup within 5 minutes in this short video!
Want to learn more?
Complete IT Systems have a team of Barracuda specialists on hand to demo the solution, discuss business benefits and help you understand how the technology works for your organisation.
To get in touch or request a demo please contact us.