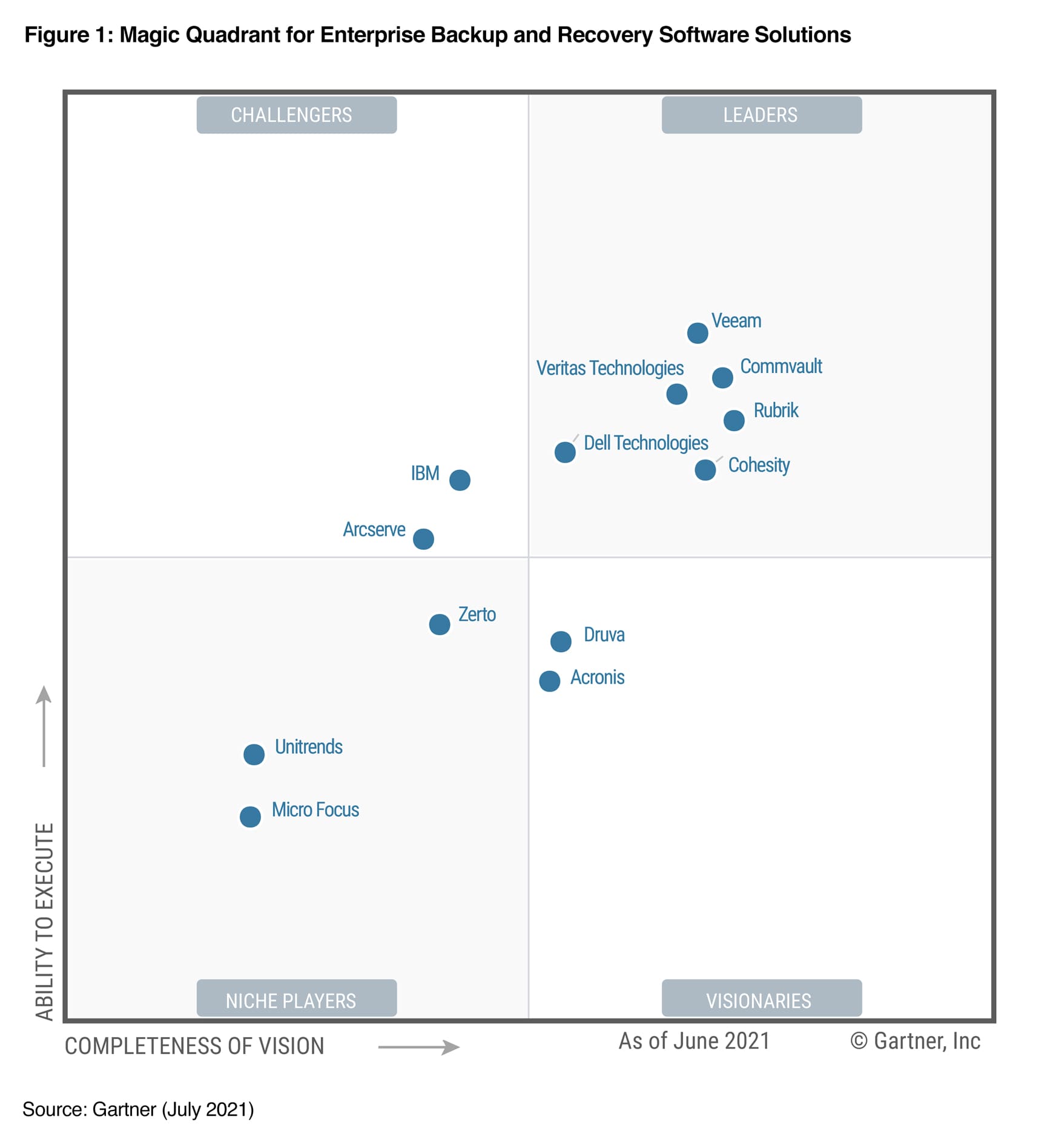
The way we interact with our money changed forever in 2020.
One of the social and technological transformations caused – or at least accelerated – by the Covid-19 pandemic was the unprecedented growth in the use of financial technology.
This surge in demand meant the fintech industry had to step up and scale fast, creating new solutions for consumers and businesses that worked for the online world, and that will go on to thrive in the new normality.
Many fintech trends were already well underway; they simply moved further along their growth curve during the pandemic.
Since then, a wave of new financial services providers has stepped in to fill that space and acquire an ever-growing market share.
Further Investment
The June 2020 AI in Fintech Market – Growth, Trends, Forecasts (2020-2025) from Research and Markets valued the global AI-in-fintech market at around £4.8 billion in 2019 and expected it to grow to over £16 billion by 2025 at a compound annual growth rate of 23.37% (2020-2025).
Initially, the small matter of a global pandemic acted a bit of a speedbump to these growth projections.
It quickly bounced back, though. According to a KPMG industry report, fintech investment doubled in H1’20 to H2’20 from £24 billion to nearly £52 billion, with global fintech-focused VC investment reaching over £30 billion in 2020.
Traditional brick-and-mortar banks as we know them may be withering (see below), but some of the institutions behind them are quietly investing in fintech: developing new brands, often through an internal startup approach, emulating the agility of the new upstart competitors in the challenger and neo banking world.
As well as acting as VCs to their internal projects, some are joining broader industry consortia to pursue more ambitious long-term goals and tackle legal and compliance issues.
Growth of Digital-only Banks
Trust in traditional financial institutions and banks never really recovered from the 2008 financial crisis.
Thanks to fintech, traditional banking is in serious decline, as a new generation of digitally native customers are turning their backs on their parents’ trusted choices.
Instead, they’re seeking solutions to their unique situations, such as a mortgage lender who understands the realities of a gig worker’s income.
Rather than turning to a big ‘high street’ bank for future services, smart consumers increasingly shop around for the best fit, because these days that can be as simple as downloading a new app.
A Boston Consulting Group survey across 15 countries showed that 44 percent of 18-to-34-year-olds had enrolled in online banking for the first time during the early weeks of the COVID-19 lockdowns.
And they’re borrowing too, from peer-to-peer micro-loans in developing nations to streamlined mortgage applications in the US.
Going Mainstream – Accessing Untapped Markets
Startups in fintech are unbundling offerings to create niche new markets, addressing inclusion issues, and often cutting costs for users through efficient use of technology.
By offering services to formerly unbanked or underbanked populations around the world, they’re growing the pie for all providers.
And with interest rates for savers so low everywhere, the perks and bonuses on offer are more attractive as a result: why wouldn’t you choose a credit or debit card with cashback or discounts at your favorite store?
Closer Regulator Scrutiny
While legislative change always lags behind technological advances, regulators are taking a growing interest in many fintech hotspots such as blockchain technologies and cryptocurrencies.
Globally the response is fragmented, with smaller and nimbler jurisdictions moving faster, while others are setting up sandboxes to test scenarios and encourage innovation.
Lawmakers are taking a keen interest in the lending side too, with growing concerns over consumer credit apps, which may encourage shoppers to spread the cost of fast fashion items over a longer period than the lifetime of the garment itself.
Embedded Finance
Powered by the Open Banking movement, embedded finance is already radically reforming the way businesses generate revenue and interact with consumers.
The ‘buy-now-pay-later’ shopping trend is obviously the most visible of these embedded finance developments. But the possibilities for disruption – and revenue generation – are virtually limitless.
Other examples range from e-wallets and instant merchant payments, to services that allow landlords and their would-be tenants to agree upon and close deals, and purchase and insurance funding in the automotive industry… to name but a few.
Artificial intelligence and machine learning cut costs, accelerate administration, and assist fraud prevention, all of which remove friction from each transaction.
The growth of technologies such as natural language processing and self-service for financial products can improve financial awareness and control for informed consumers. But it can equally be used to target naïve stock traders or reckless bargain hunters.
Autonomous Finance & the Opening Up of Financial Services
Beyond developments in embedded finance, fintech startups continue their tendency to democratise accessibility to typically gate-kept financial services, like day trading and forex.
Today, consumers around the world are now trading stocks, exchanging currencies, sending remittances, and contracting for retirement investments, all without involving traditional financial institutions in any way.
In parts of the world suffering financial crises – from credit crunches to hyperinflation – these tools are already providing a lifeline to tech-savvy consumers.
In more financially privileged environments, furloughed workers get to dabble in new things to do with their stimulus payments.
For better or worse, we will doubtless see further Gamestop scenarios playing out, as fintech puts powerful financial tools in the hands of every smartphone holder.
The rise of RPA
As with so many other developing areas of technology, robotic process automation (to give it its full name) is set to bring root and branch disruption to fintech in the coming years.
Whether it’s customer onboarding, data entry or reporting, or even insurance claim checks or processing an individual’s suitability for a loan application, if it’s a task that’s repetitive in nature, then the chances are that RPA will be stepping into the breach before too long.
The Central Role of Cybersecurity
With far-reaching disruption and ever-increasing digitalisation – from machine learning and AI to 5G and IoT – cybersecurity threats have never been greater.
As a result, the cybersecurity market is projected to grow from £118bn in 2021 to over £266bn in 2028.
Central Bank Digital Currencies
Contactless payments exploded in 2020, moving out of the e-commerce realm into face-to-face transactions for all generations, as everyone tried not to touch anything.
This cash decline coincides not only with all-time highs for bitcoin, but also a high level of interest in central bank digital currencies, and other far more ‘alternative’ digital options.
With its digitalisation of the renminbi in April 2021, China was the first of the major global economies to break cover and make the jump into the unknown world of CBDCs.
One thing’s for sure: it certainly won’t be the last – particularly as there’s already excited talk of the move hastening the “decline of the dollar’s dominance as the world’s leading reserve currency”.
The End of Cash?
The way we pay for things has irreversibly changed, and fintechs are jumping on this trend, again responding to changes in the social environment.
Even as far back as 2018, Pew Research found that just over a third of US adults under the age of 50 made no weekly cash purchases.
More recently, the National Retail Federation and Forrester Research indicated 19% of US consumers made a contactless digital payment for the first time in May 2020.
Usage of apps like PayPal, Square and Apple Pay has surged as consumers increasingly looked to reduce their cash usage in the wake of COVID-19.
Combined with further mainstream uptake of decentralised cryptocurrencies like Bitcoin and Ethereum, and the rise of CBDCs (see above), it’s fair to say that the writing’s on the wall for cash.
Now we just need smartphone facial recognition technology that recognises you through a face mask when you get to the checkout… but that will come soon.
In Conclusion
So as with almost everything else the present and future of finance – in 2021 and beyond – is tech.
It’s a fragmented, competitive, and not always well-regulated world of alternatives, where consumers will have more choice to navigate a fast-changing fintech landscape.
In the process, they’ll be equipped to take charge of their money management like never before.
About the Author:
As a market research veteran and founder of NYC-based B2B market research consultancy firm, Adience, Chris Wells has worked with hundreds of fintech companies over the years.
Links:
https://assets.kpmg/content/dam/kpmg/xx/pdf/2021/02/pulse-of-fintech-h2-2020.pdf
https://www.bcg.com/en-es/publications/2020/covid-19-causes-a-new-outlook-on-pricing-and-revenue-for-banks
https://www.marketdataforecast.com/market-reports/ai-in-fintech-market
https://www.pewresearch.org/fact-tank/2018/12/12/more-americans-are-making-no-weekly-purchases-with-cash/
https://www.ft.com/content/3fe905e7-8b9b-4782-bf2d-fc4f45496915
https://www.hello-adience.com/fintech/